Introduction: In the ever-evolving landscape of cybersecurity, staying updated with the latest protocols and server configurations is paramount. As TLS 1.3 takes center stage in security, recent updates from Microsoft bring both opportunities and challenges for ensuring connectivity. This blog delves into the significance of TLS 1.3 alongside Microsoft’s server update, shedding light on their impact and implications.
TLS 1.3: A Security Paradigm Shift: TLS 1.3, the latest evolution in secure communication protocols, offers heightened security and improved efficiency. Its emphasis on modern cipher suites and streamlined handshake processes has made it a cornerstone of secure data transmission across networks.
Microsoft Server Update and TLS Retirement: Microsoft’s proactive move to retire TLS 1.0 and 1.1 within Azure indicates a crucial step toward security. However, this update also necessitates adaptations to ensure continued connectivity for applications reliant on older TLS versions.
Impact on Availability Tests in Azure Monitor Application Insights: As part of this update, Availability Tests in Azure Monitor Application Insights will transition to communicate using TLS 1.3. This phased update, rolling out between December 2023 and March 2024 across specific regions, may prompt connectivity issues for tests monitoring remote endpoints with misconfigured or outdated TLS implementations.
Managing Connectivity Issues: Users may encounter errors such as “The request was aborted: Could not create SSL/TLS secure channel” during this update. To rectify this, ensuring that endpoints are accessible by clients running Windows Server 2022 with TLS 1.3 enabled becomes imperative.
Adapting to the Changes: For those experiencing challenges in promptly configuring TLS 1.3 on their endpoints, Microsoft suggests temporary disabling of TLS 1.3 to allow Availability Tests to fall back to older TLS versions. This provides a window for making necessary adjustments while ensuring continued functionality.
Understanding TLS 1.3:
TLS, the successor to SSL (Secure Sockets Layer), has evolved over the years to address vulnerabilities and enhance security measures. TLS 1.3 represents the latest iteration, significant improvements over its predecessors. Its primary goal is to enhance security while the handshake process, reducing latency, and encryption algorithms.
Importance of TLS 1.3:
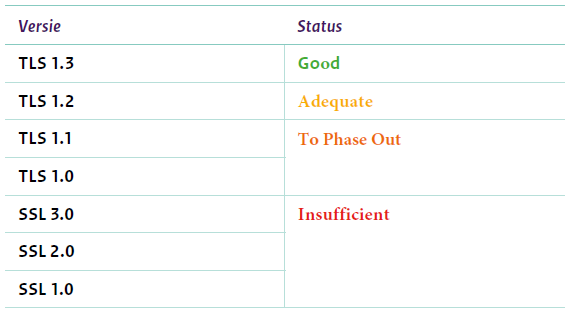
- Enhanced Security: TLS 1.3 prioritizes modern cryptographic algorithms, eliminating outdated and vulnerable options. This significantly reduces the attack surface and enhances overall security.
- Performance Boost: By optimizing the handshake process and reducing round trips, TLS 1.3 improves connection times, benefiting both users and servers.
- Forward Secrecy: This feature ensures that past communications remain secure even if long-term encryption keys are compromised in the future.
- Resistance to Attacks: TLS 1.3 addresses known vulnerabilities present in earlier versions, making it more resilient against attacks like protocol downgrade attacks and padding oracle attacks.
Cipher Types in TLS 1.3:
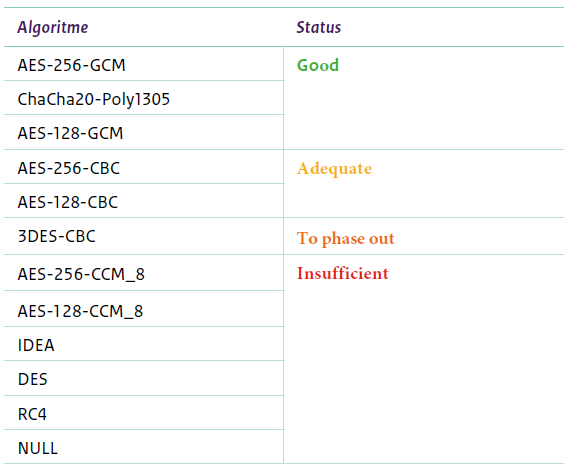
Cipher types are selected based on security, performance, and compatibility requirements. In secure communication protocols like TLS, a combination of cipher suites (which include specific encryption, authentication, and key exchange algorithms) is negotiated during the handshake between client and server to determine the most secure and efficient method for communication. The chosen cipher suite dictates how data will be encrypted, decrypted, and authenticated during the secure communication session.
- ChaCha20-Poly1305: This authenticated encryption algorithm offers high performance and security, especially on devices without hardware support for AES encryption.
- AES-GCM and AES-CCM: Advanced Encryption Standard (AES) in Galois/Counter Mode (GCM) or Counter with CBC-MAC (CCM) offers robust encryption and authentication, commonly used in TLS 1.3.
- Elliptic Curve Diffie-Hellman (ECDHE): ECDHE key exchange algorithms provide forward secrecy, enabling secure communication without compromising past sessions even if private keys are exposed in the future.
HMAC Algorithms and Hash Functions
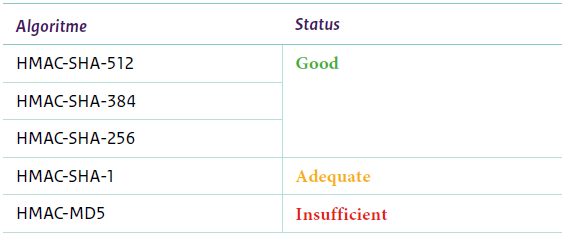
Hash-based Message Authentication Code (HMAC) is utilized within TLS and SSL for integrity checks and authentication. HMAC algorithms, combined with robust hash functions, provide a means to verify that transmitted data remains unchanged and originates from an authenticated source.
Historically, TLS and SSL implementations favored hash functions like SHA-1 and MD5 for HMAC operations. However, due to vulnerabilities and the emergence of more secure options, modern TLS versions prioritize stronger hash functions such as SHA-256, SHA-384, and SHA-512, enhancing the overall security of the protocol.
1. HMAC-SHA-512 (Hash-based Message Authentication Code with SHA-512):
- Algorithm: HMAC-SHA-512 utilizes the SHA-512 hash function coupled with HMAC for authentication.
- Strengths: Provides security due to SHA-512’s 512-bit hash output, offering high resistance against collision and preimage attacks.
- Usage: Often employed in applications requiring top-tier security, although it might introduce higher computational overhead due to its larger hash size.
2. HMAC-SHA-384 (Hash-based Message Authentication Code with SHA-384):
- Algorithm: Similar to HMAC-SHA-512, but using SHA-384 for hashing.
- Strengths: Offers strong security with a 384-bit hash output, balancing security and computational efficiency compared to SHA-512.
- Usage: Suitable for scenarios demanding high security while considering computational performance.
3. HMAC-SHA-256 (Hash-based Message Authentication Code with SHA-256):
- Algorithm: Employs the widely used SHA-256 hash function in conjunction with HMAC.
- Strengths: Provides a good balance between security and performance, delivering a 256-bit hash output.
- Usage: Commonly utilized in various applications due to its robust security and efficient computation.
4. HMAC-SHA-1 (Hash-based Message Authentication Code with SHA-1):
- Algorithm: Uses the SHA-1 hash function with HMAC for authentication.
- Considerations: While historically prevalent, SHA-1 is now considered weak due to known vulnerabilities, making HMAC-SHA-1 susceptible to collision attacks.
- Usage: Deprecated in many security-sensitive applications due to security concerns.
5. HMAC-MD5 (Message Digest Algorithm 5):
- Algorithm: MD5 was widely used in the past but is now deemed insecure due to vulnerabilities and collision attacks.
- Considerations: Prone to collisions, where different inputs can produce the same hash output, compromising security.
- Usage: Highly discouraged in modern applications due to its vulnerabilities, replaced by more secure hash functions.
TLS and HMAC Selection: In TLS 1.3, the choice of HMAC algorithms impacts the security of data transmission during the handshake and communication. Modern TLS implementations prioritize stronger hash functions like SHA-256, SHA-384, and SHA-512 due to their resistance against attacks compared to SHA-1 and MD5.
Transitioning to Secure HMAC Algorithms: The deprecation of weaker hash functions like SHA-1 and MD5 in favor of stronger alternatives underscores the ongoing evolution toward enhanced security in cryptographic protocols like TLS.
Conclusion: The convergence of TLS 1.3 and Microsoft’s server updates signifies a proactive stride toward a more secure digital environment. Embracing TLS 1.3 while navigating the transitional phase with Microsoft’s server updates ensures not only enhanced security but also a resilient infrastructure for future advancements.
Closing Thoughts: As TLS 1.0 and 1.1 retire, and TLS 1.3 becomes the benchmark for secure communication, enterprises, and users must prioritize adaptation. This not only guarantees uninterrupted services but also reinforces a robust security posture in an ever-evolving digital ecosystem.